Excis Compliance Ltd.
Ocean House,
Bracknell Enterprise and Innovation Hub
The Ring, Bracknell
RG121AX
United Kingdom
Partners
ISO Certfications Certified Covering The UK




The numerous advantages of today’s increasingly digitized and interconnected world come with a price: Cyberattacks have become a serious threat – affecting our real-life and not only just data anymore. Comprehensive security mechanisms and a security-oriented mindset throughout the entire organization are essential to avert and control this risk.
Cybersecurity is the ultimate program that helps to defend your organization against any data breach easily. In the modern-day, every organization prefers a better way to easily protect their data from theft or damage from irresistible targets for cybercriminals. Cybersecurity involves securing the
Sensitive data
Protected Health Information (PHI)
Intellectual property
Personally Identifiable Information
Critical Data
Governmental and Industrial Information Systems
Cybersecurity:
Cyber threats are everywhere, and are constantly changing.It’s almost impossible for most businesses to maintain a fully staffed, full time, on site IT security department that can provide the cyber strategy and protection needed today. At Excis, we offer affordable, comprehensive cyber security solutions and cybersecurity consulting services for businesses of all sizes. Our in-house team of cybersecurity consultants protect your data, make sure you meet compliance requirements, and give you confidence that your business is safeguarded. Some of the strategies include
End point protection
Data encryption & protection
Network protection
Data Privacy
Network Security:
Network security is any activity designed to protect the usability and integrity of your network and data. It includes both hardware and software technologies that target a variety of threats and stop them from entering or spreading on your network. Effective network security manages access to the network.
End point security:
Excis offers design and consultation of industry standard end point security solutions end point security solutions that go beyond traditional antivirus.
Web Security:
Excis Web Security Solution protects users on any device, anywhere. With zero downtime while onboarding and a combination of always-on security and expert-created, surgically accurate security rules, our web app firewall assures zero false-positives and ensures applications are always protected. Excis sits between the web services and the clients. The requests from clients are routed through the application web firewall, where monitors take place for questionable behavior. It checks the header and contents of the requests. By enforcing a set of pre-defined rules, the cloud firewall filters what parts of the communication are malicious and what parts are benign.
Email Security:
Email security is important because email contains sensitive information, is used by everyone in the organization, and is therefore one of a company’s largest targets for attacks. The shift to cloud-based email like Gmail and others comes with several benefits, but cloud-based email has become a tempting attack surface for cyber criminals.
Hybrid Cloud Security:
Excis provides a hybrid cloud security solution that protects the data, applications, and infrastructure associated with IT architectures. It incorporates some workload portability, orchestration, and management across multiple IT environments, including at least one public or private cloud.
Products & Solutions from the OEM:
There are many methods suitable for easily increasing security along with reducing the risk of cybercrime.
Penetration testing
Packet sniffers
Firewall tools
Encryption tools
Web vulnerability scanning tools
Antivirus software
Network security monitoring tools
Intrusion Prevention and Detection
Protect Your Sensitive Data:
Investing in the right tools limits information loss and is also a suitable option for monitoring the 3rd party risk and 4th party vendor risk. Normally, continuous scanning for data exposure would be a suitable option. When there is any data leak and left unattended, then the cybercriminals can gain access to all internal networks.
Implement A Third-Party Risk Management (TPRM) Solution:
With the use of advanced technology and tools, it is a convenient option for reducing the costs such as sending out vendor assessment questionnaires automatically. Below are some of the practical strategies to reduce the cybersecurity risk
Identity access management
Extended detection and response
Fraud protection
Data security
Mainframe security
Mobile security
Eliminate threats faster
File Protect
Fully integrated and enterprise-grade security suite
Educate Staff:
Human Error has been causing more than 90% of the Data breaches. Based on the recent statistics, these could lead to a silver lining. It helps to fix the problem when staff members are instructed on how to recognize cyber threats. Educational programs increase the value of all cybersecurity solution investments in the organization.
Educate Staff:
Human Error has been causing more than 90% of the Data breaches. Based on the recent statistics, these could lead to a silver lining. It helps to fix the problem when staff members are instructed on how to recognize cyber threats. Educational programs increase the value of all cybersecurity solution investments in the organization.
Managed Services / Professional Consultancy:
Excis is the leading all-in-one destination for solving International IT needs. The well-managed team at Excis with international standards provides the right resources to the customers. Organizations can utilize 24/7 support services with the provision of end-to-end solutions. In-house experts are well versed in handling Cybersecurity solutions.
Normally, the core service includes the on-site, end-user, as well as network services that are delivered globally through scheduled support or instant dispatch. Whether you are looking to manage risk or accelerate business innovation, then hiring the expert team at Excis is the convenient option.
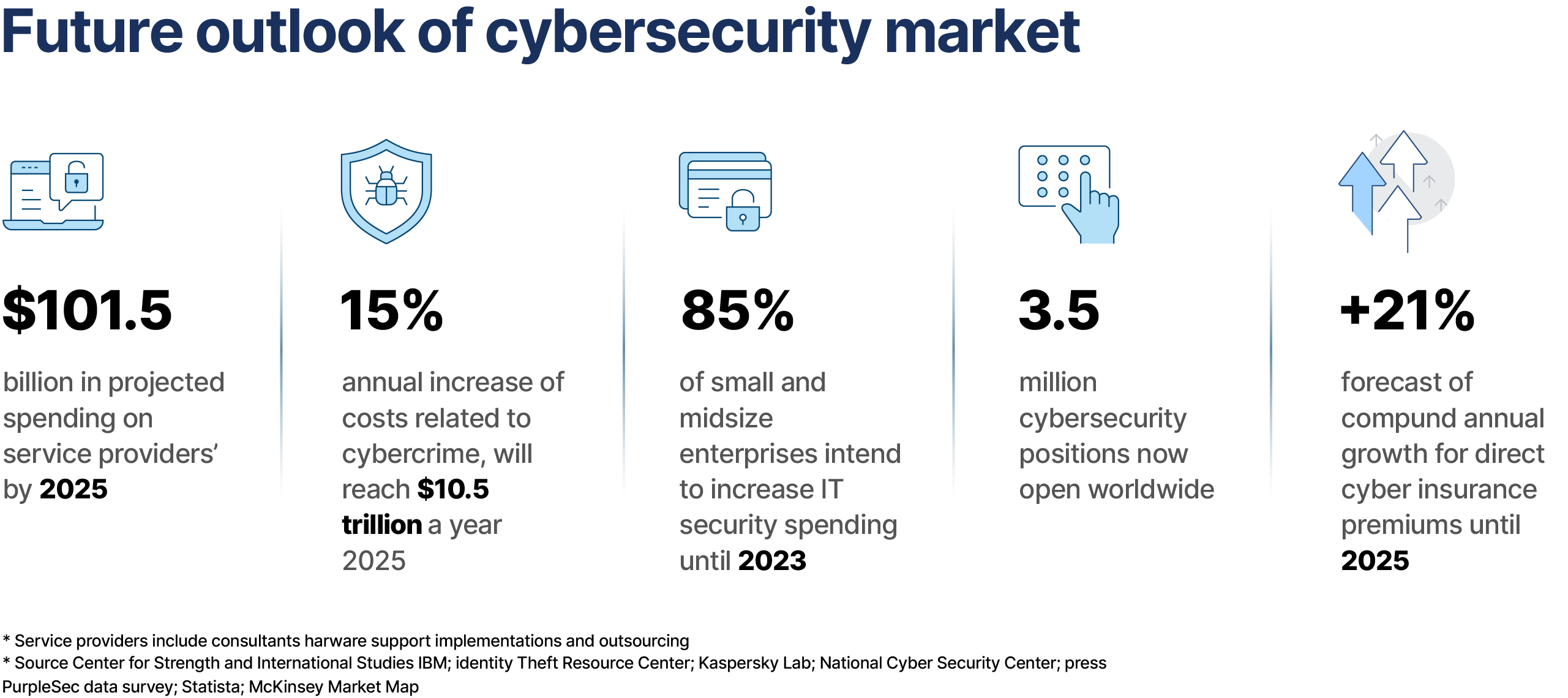
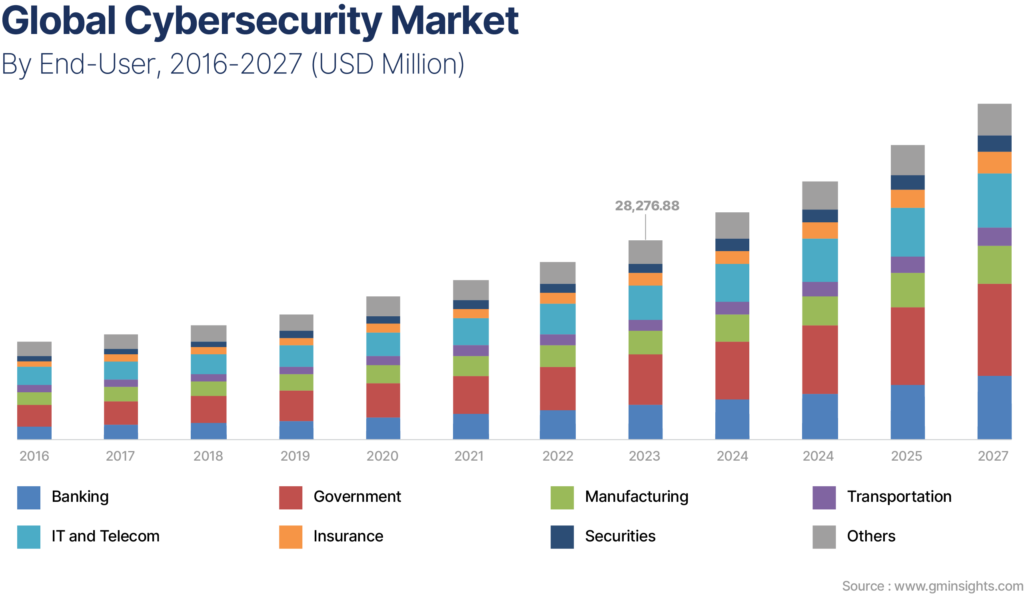
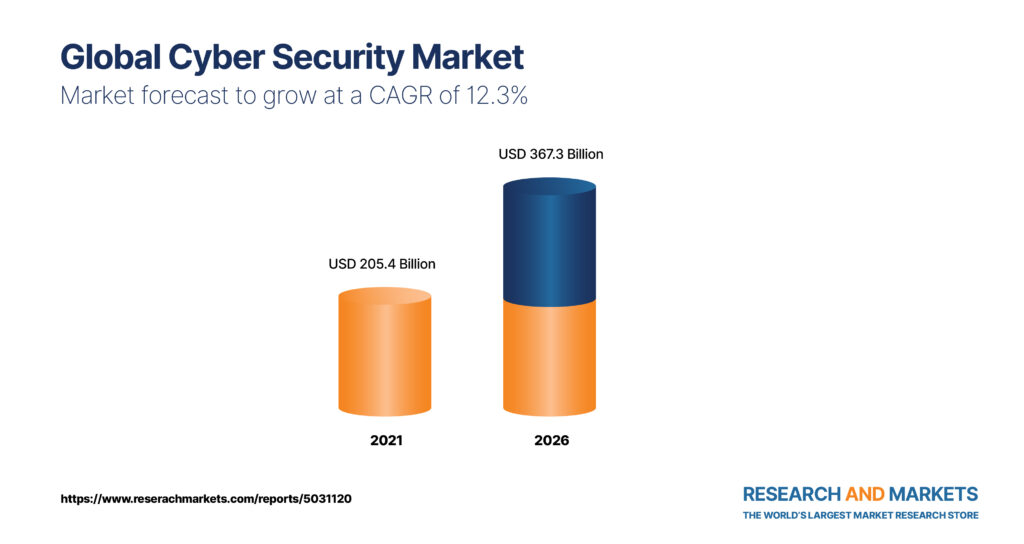
Return on Investment 2022:
Companies are prioritizing significant investments in regulatory compliance efforts to gain immunity from risks that surround security breaches. In line with this, the global cyber security market value surpassed US$ 100 Bn in 2018 and will see stupendous growth at a double digit CAGR during the forecast period (2016-2027).
Excis uncovers threats with innovative correlating incident data. Experts’ team applies unparalleled frontline intelligence as well as analytics. It would be suitable for easily gaining threat detection and investigation along with the high-end incident response. Excis Integrates as well as automates technologies across your IT infrastructure. So it is a suitable option for making your data highly secure in all aspects.
Innovative Security Platform:
With the industry’s broadest portfolio, Excis can help you quantify as well as prioritize your risks. You can easily get complete consulting as well as globally managed security services. Professionals are ready to deliver industry-leading assessments with the best innovative security strategies. These are suitable options to detect and respond to threats.
24/7 Support Desk
Global Presence
Delivered via three global service centers
Business Performance and Scalability
True integration and solutions
Organization’s security architectures
Delivers unparalleled protection
Visibility to the network segment
End-to-end design
Established supports
Planning and consultation on network
Positioned to provide uninterrupted cover
Assist with ensuring an end to end cyber security solutions
Designed and tailored by qualified technical solution teams
Value chain expanded
Increases your resilience against cyber threats
Endpoint Security And Managed Services:
At Excis, our experts offer comprehensive endpoint defense that extensively protects the user from any threats. It is also a convenient option for detecting advanced attacks with empowering the responses. Our team would create cybersecurity tailored to specific business needs. It is a suitable option for defending against cyberattacks and industry-relevant threats. Advanced systems would provide better confidence in making your business secure.
Identify:
In order to manage and reduce the cybersecurity risk to the systems and assets, experts establish the organizational plan.
Protect:
Get the zero trust-based approach for protecting the data with advanced hybrid cloud infrastructure.
Detect:
Our experts manage the defenses against attacks by collecting complete, actionable insights. They would identify security events using advanced, powerful AI-driven tools.
Excis Compliance’s integrated Cybersecurity solutions also include consulting that covers technological, procedural, and personal elements and comprehensive services throughout the entire lifecycle of the assets. Our experts for Cyber Security Services are your reliable partner and accompany you through the entire process to protect the productivity and availability of your system – because digitization and cybersecurity go hand in hand.
Ocean House,
Bracknell Enterprise and Innovation Hub
The Ring, Bracknell
RG121AX
United Kingdom



